 Introduction to (Open)SCAP
Introduction to (Open)SCAP
SCAP stands for Security Content Automation Protocol. It is an open standard which defines methods for security policy compliance, vulnerability management and measurement etc. This article focuses on the operating system compliance part of SCAP.
It comes originally from the US National Institute of Standards and Technology (NIST) to provide a way for US government agencies to audit its systems for regulatory compliance.
OpenSCAP is a NIST validated open source implementation of SCAP.
Why should I make use of OpenSCAP anyway?
Lot of people will ask this question to them self, in particular System Administrators and Engineers since they are not IT Security Officers.
The simple answer is that you just sit down with the IT Security Officer once and define which systems need to be compliant to what regulatory, With OpenSCAP you can always ensure the systems are configured according the the policy (or policies).
Organizations that need to be compliant according to a official policy will sooner or later facing an external security audit. I experienced that several times, its a nightmare. If you can proof that your systems are scanned regularly with the SCAP standard, you will be very well prepared, an external auditor will not bug you for a long time.
Abbreviations, abbreviations, abbreviations
Its obvious, government agencies love abbreviations 😉 Lets explain the two most important ones.
XCCDF
Extensible Configuration Checklist Description Format. This files, i.e. /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml contain descriptions used for auditing a system against compliance to a policy.
This files are usually included in your distribution and are updated if needed.
OVAL
Open Vulnerability and Assessment Language. Its used to detect vulnerabilities and patches.
Since vulnerabilities and patches are popping up very quickly they need to be downloaded and distributed to all systems to be audited on a regular base (i.e. daily).
OVAL files can be downloaded as listed below:
- RHEL7 https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL7.xml
Debian https://www.debian.org/security/oval/oval-definitions-2017.xml- Debian https://www.debian.org/security/oval/
- Suse (SLES 12) http://ftp.suse.com/pub/projects/security/oval/suse.linux.enterprise.server.12.xml
- Ubuntu 16.04 LTS https://people.canonical.com/~ubuntu-security/oval/com.ubuntu.xenial.cve.oval.xml
Organizations using System Management Tools such as Red Hat Satellite or SUSE Magager will not profit from OVAL patch scans as those products will report which patches have been applied or not by themself. Nevertheless, additional OVAL scans add the benefit of vulnerability scanning regardless of installed patches.
More Abbreviations
More abbreviations and a short description of them can be found here: https://www.open-scap.org/resources/acronyms/
OpenSCAP Scap Security Guide (SSG)
There are a lot of regulations out there. Government of some countries releases policies and sometimes SCAP content for some Operating Systems, mostly RHEL and Windows. The SSG Project works on collecting and implementing content for this policies for the operating systems as well as for some other software such as JBoss. Included in the scap-security-guide are the most important US Government and PCI-DSS for RHEL. Only available for Debian at the moment is the content for the French ANSSI DAT-NT28.
The only Linux distributions I’m aware of that provides packages for scap-security-guide are RHEL and Fedora. However, upstream there is some content for more distributions available. I really hope that all important and fine distributions such as SLES, Debian and Ubuntu will jump on the bandwagon.
Regulations covered by OpenSCAP SSG
Here a list of what is available for the most important Linux distributions.
Red Hat Enterprise Linux 7
- PCI-DSS (Payment Card Industry – Data Security Standard), Commercial – USA
- C2S (Commercial Cloud Services), Government – USA
- USGCB/STIG (United States Government Configuration Baseline/Security Technical Implementation Guide), Government – USA
- CNSSI 1253 (Committee on National Security Systems), Government – USA
- CJIS (Criminal Justice Information Services), Government – USA
Debian and Ubuntu
Officially there is nothing available. Its is currently under development, see https://github.com/OpenSCAP/scap-security-guide/tree/master/Ubuntu/16.04 and https://github.com/OpenSCAP/scap-security-guide/tree/master/Debian/8.
As of 2017-03-04 compiling fails.
- ANSSI DAT-NT28 (Agence nationale de la sécurité des systèmes d’information), Government – France
Suse Linux Entrprise Server
Suse does not provide the scap-security-guide package and there is no XCCDF content for regulatory compliance checks delivered by Suse. However, some basic tests are available. It is not clear if Suse has some plans to join the scap-security-guide community, would be nice to see that. SLES customers can open a support case at https://scc.suse.com/login and ask for enhancement.
Using SCAP content without scap-security-guide
You can make use of SCAP content without the OpenSCAP security guide. Its rather complex and not covered in this article.
Installing the required packages
RHEL 7
[root@server ~]# yum -y install scap-security-guide
All required dependencies will be installed as well
Debian and Ubuntu
root@ubuntu:~# aptitude install python-openscap
All required dependencies will be installed as well
SLES12sp2
sles12sp2:~ # zypper install openscap openscap-content openscap-extra-probes openscap-utils
All required dependencies will be installed as well
Tailoring profiles
For most users it is probably too much to secure its systems according to military standards which includes turning off USB support and the like.
The most important civil regulatory by far is PCI-DSS. Each company handling kind of Credit- or Debitcard data must obey the current standard. As of writing this article this is version 3.2.
PCI-DSS is a de-facto standard in Enterprise Linux environments.
Of course it makes sense for all kind of companies to secure its systems. On systems which are not exposed, security policies can be more relaxed.
Also good to know is that some tests simply do not apply to your system. I.e. if you are using a centralized identity management software such as Redhat IdM with IPA or Microsoft Active Directory then the central instance will take care about the password policies, not the particular system to be audited.
Installation of the SCAP Workbench
The Scap Workbench is available in RHEL to be installed by yum, a binary for Windows and Mac OS is available as well. Needless to say that the source code is available.
Downloads: https://github.com/OpenSCAP/scap-workbench/releases
Usage
In the following examples, we disable the check for AIDE.
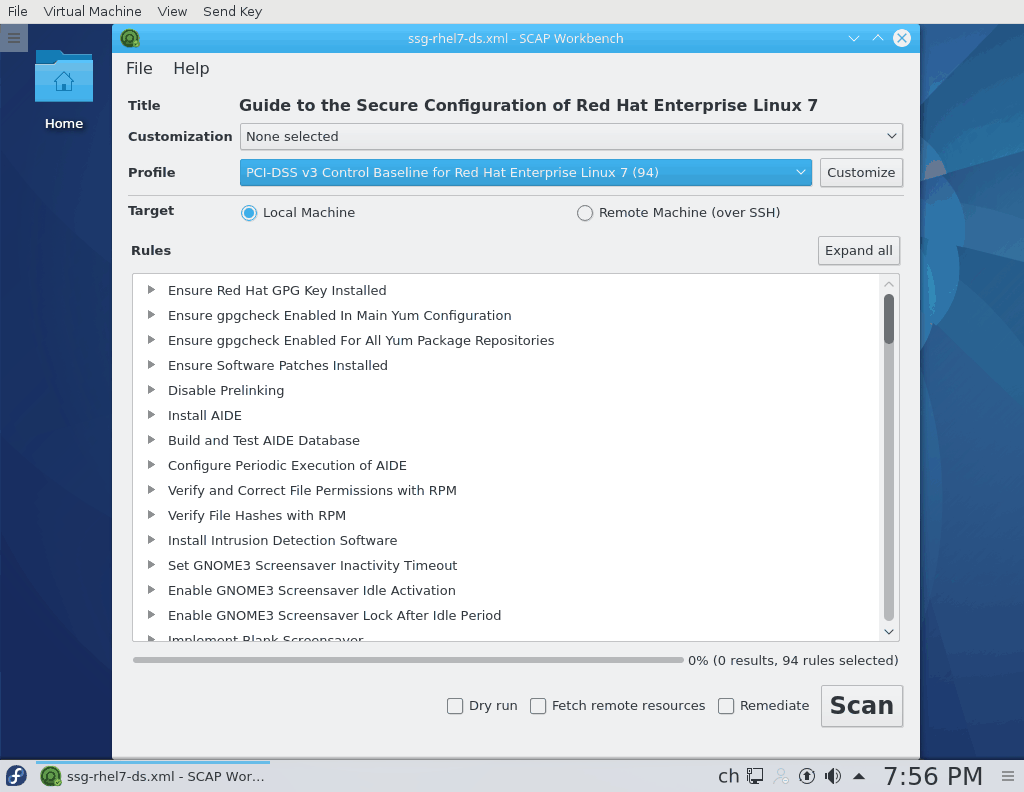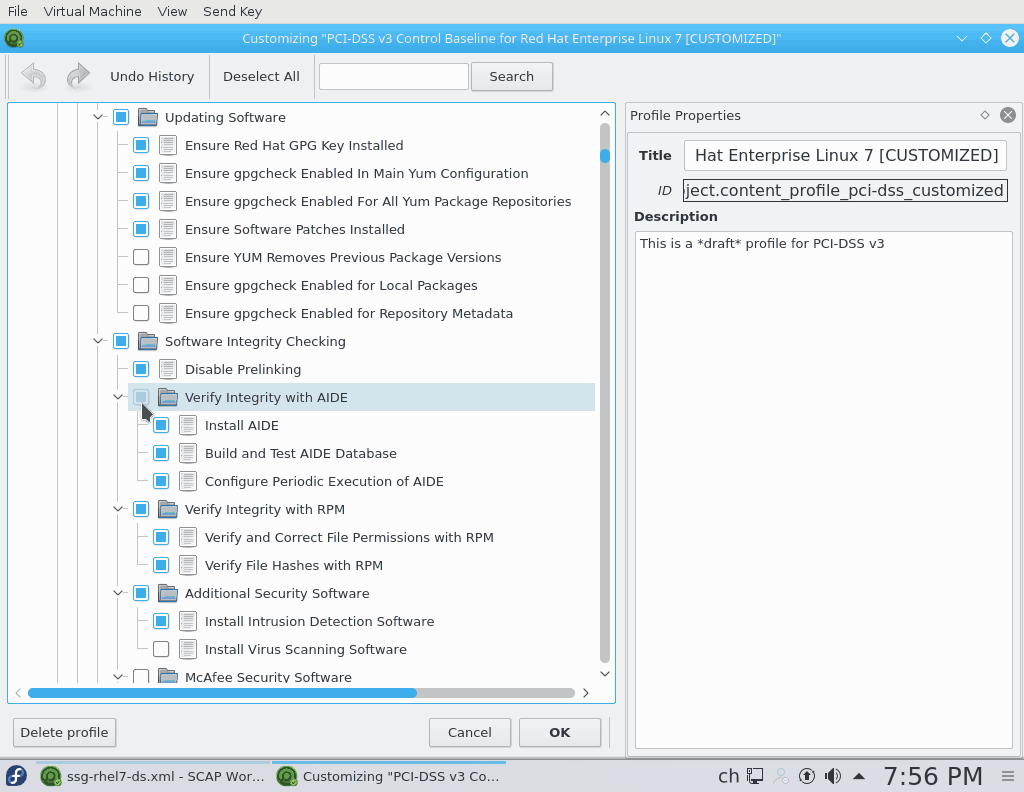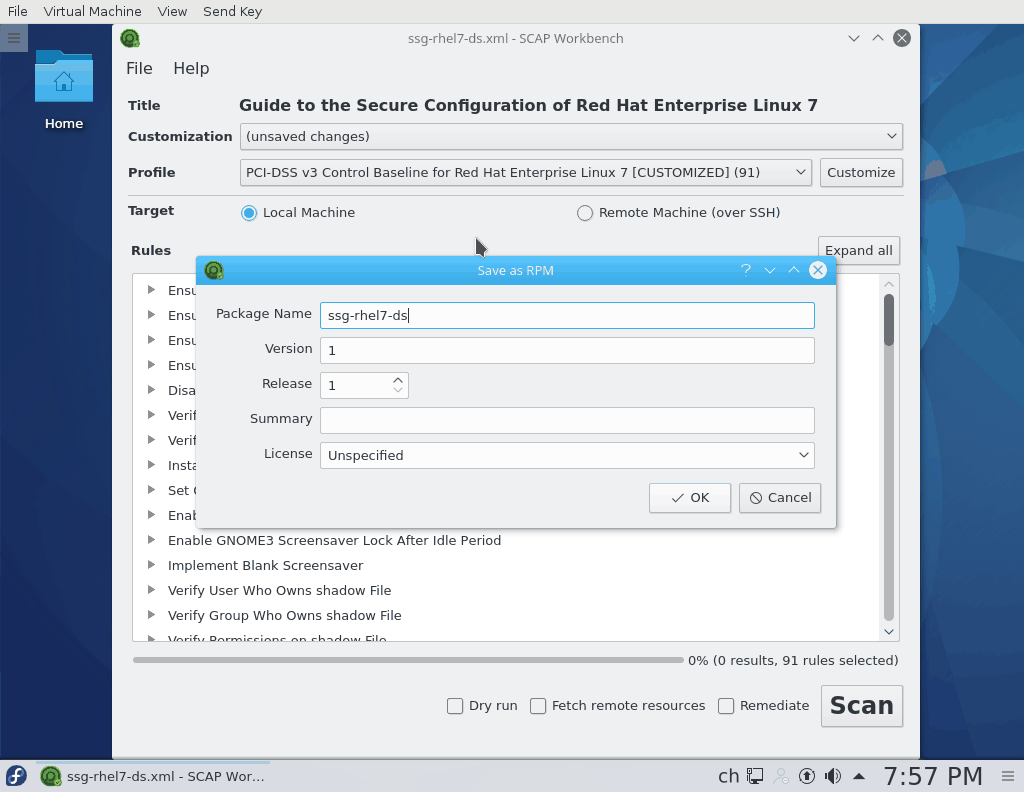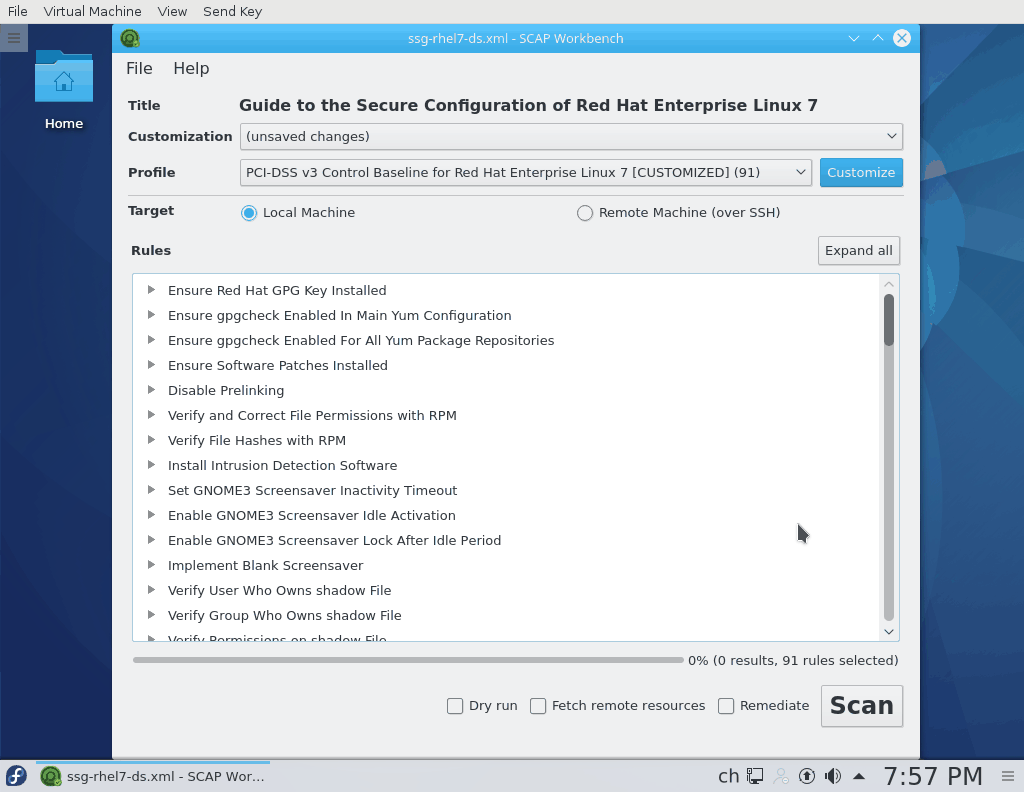
You can save the tailoring file as a single XML file or even better safe it as an RPM for easy distribution to all your systems.
Scanning
The usage is the same on all tested Linux distributions. Be aware, XCCDF scanning makes no sense w/o any SCAP content. If your distribution does not provide you the necessary data, 3rd party providers may.
RHEL 7 comes with the scap-workbench which is GUI that allows you to scan the local or remote systems via SSH. The scap-workbench is a nice tool to scan a handful of servers manually but not to scan a whole zoo of servers.
You also can scan your systems with the CLI on the host itself. Kind of automation can be done with i.e with Ansible.
Manual Scan
The oscap info command gives you an overview which profiles are available.
[root@server ~]# oscap info /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml
Document type: XCCDF Checklist
Checklist version: 1.1
Imported: 2017-02-14T13:33:08
Status: draft
Generated: 2017-02-14
Resolved: true
Profiles:
standard
pci-dss
C2S
rht-ccp
common
stig-rhel7-workstation-upstream
stig-rhel7-server-gui-upstream
stig-rhel7-server-upstream
ospp-rhel7-server
nist-cl-il-al
cjis-rhel7-server
Referenced check files:
ssg-rhel7-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-rhel7-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
http://www.redhat.com/security/data/oval/Red_Hat_Enterprise_Linux_7.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
[root@server ~]#
Lets choose pci-dss and start a scan:
[root@server ~]# oscap xccdf eval --profile pci-dss --results scan.xml --report scan.html /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml Title Ensure Red Hat GPG Key Installed Rule ensure_redhat_gpgkey_installed Ident CCE-26957-1 Result pass Title Ensure gpgcheck Enabled In Main Yum Configuration Rule ensure_gpgcheck_globally_activated Ident CCE-26989-4 Result pass [Lot of Output immited]
The parameter –results saves the result in a HTML file.
Automated scanning with Redhat Satellite 6
Users of Redhat Satellite 6 can schedule scans of large server farms. The screenshots shows you how compliance tests can be presented to a IT Security Officer.
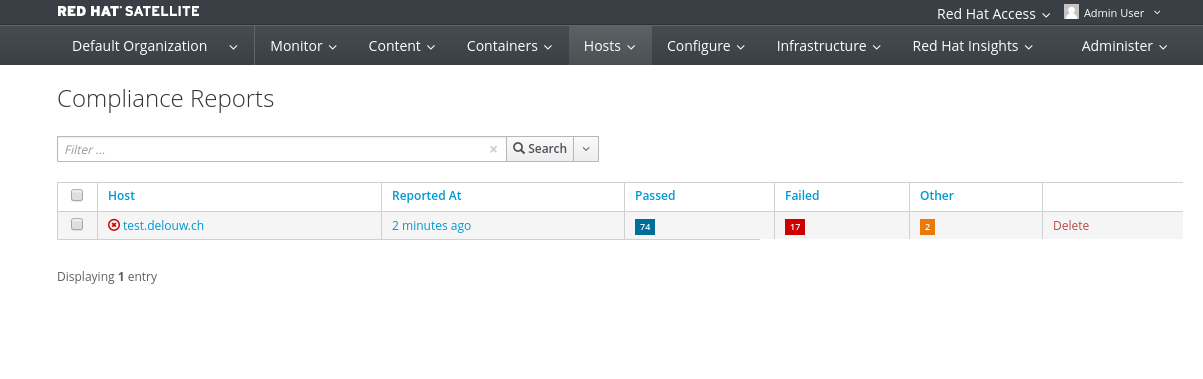
The Compliance report shows a overview of hosts and a brief look at how many test have been failed.
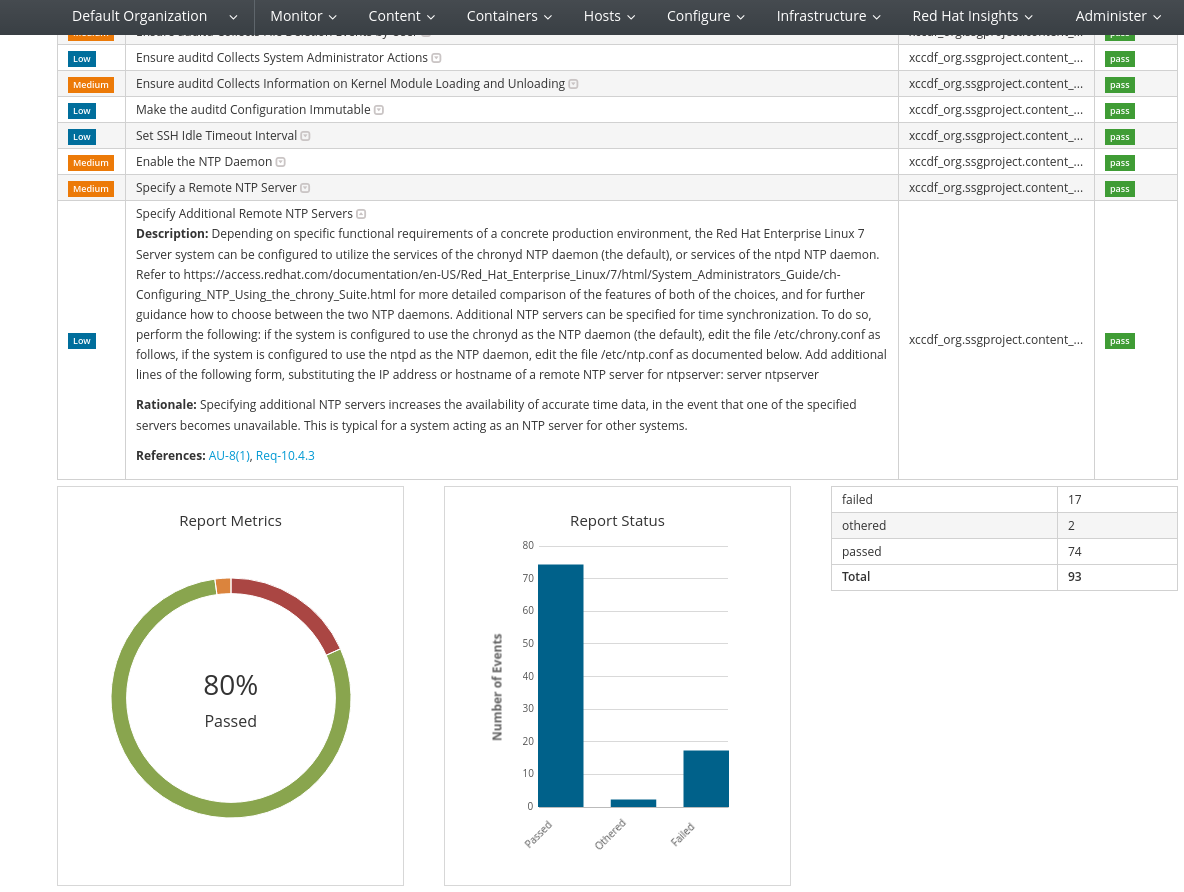
The Compliance report detail shows which test have been failed. It also provides a description of each topic.
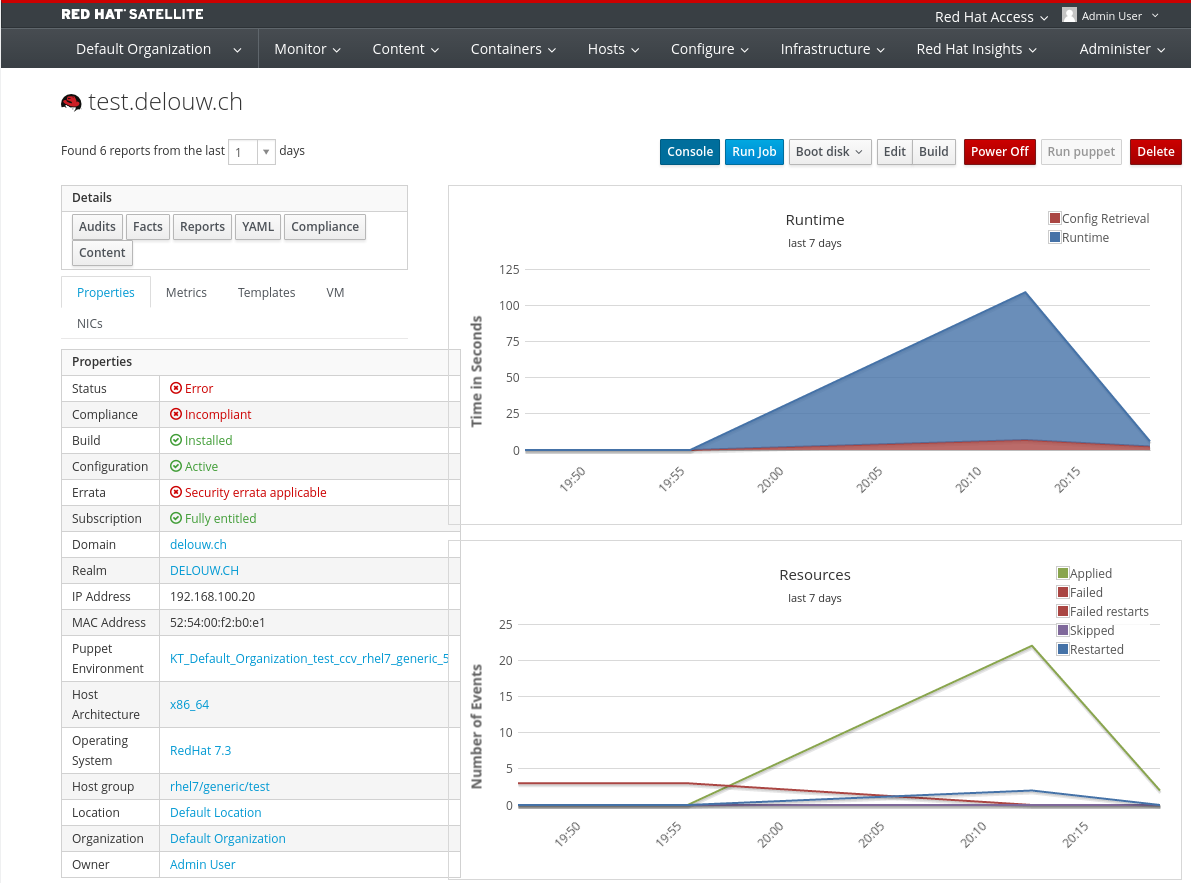
The detail view of a host shows that this host is not compliant. In this case, security errata must be applied and the host must be reconfigured to get compliant to the security policy.
Alternatives to OpenSCAP
There are a few alternatives to OpenSCAP as listed by the NIST’s Security Content Automation Protocol Validated Products.
Further reading
- OpenSCAP project website https://www.open-scap.org
- OpenSCAP security guide upstream project website https://github.com/OpenSCAP/scap-security-guide
- SCAP Website of the NIST https://scap.nist.gov
- Redhat Security Guide https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7/html/Security_Guide/sect-Using_oscap.html
- SCAP Guide for Debian https://wiki.debian.org/SCAPGuide
- SUSE Manager 3 OpenSCAP Documentation https://www.suse.com/documentation/suse-manager-3/book_suma_reference_manual/data/ch-openscap.html
Hello Luc
I’m wondering why the DAT-NT28 is not available on RHEL system ?
What’s missing and how can we help to make this available ?
Stephane.
Hi Stephane,
I just filed an RFE for adding that to SSG. See https://bugzilla.redhat.com/show_bug.cgi?id=1497415
Please add your use case to that BZ, it helps the engineers to understand the need.
Thanks
Hi there.
Your link to the Debian OVAL is invalid. Too bad, I’m trying to find a policy for my ubuntu 16 systems. Just an FYI.
Great job on this blog.
Hi,
Looks like the Debian links has changed, I updated the articel, thanks for reporting. The Links for Ubuntu 16.04 is still valid: https://people.canonical.com/~ubuntu-security/oval/com.ubuntu.xenial.cve.oval.xml
Cheers,
Luc
Hi,
Thank you for your article and, in advance, for bringing support for ANSSI DAT-NT28 in OpenSCAP for RedHat7 profiles.
Best Regards.
If you want to see ANSSI DAT-NT28 in RHEL7, please open a supportcase with Redhat were you describe the usecase. And it is not me who brings that in, it is the developer team that takes care about the further development
can i get a guide on how can I run Openscap on ubuntu linux and openstack installed over it (using devstack)? Many Thanks.
There is only little information about the topic. Please see here: https://wiki.debian.org/SCAPGuide maybe that will work for Ubuntu as well